前言
以前做的题,这题似乎有点小迷惑?
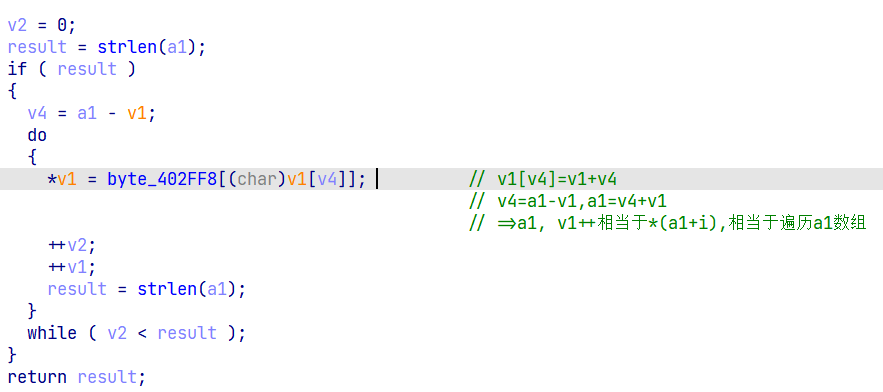
题解
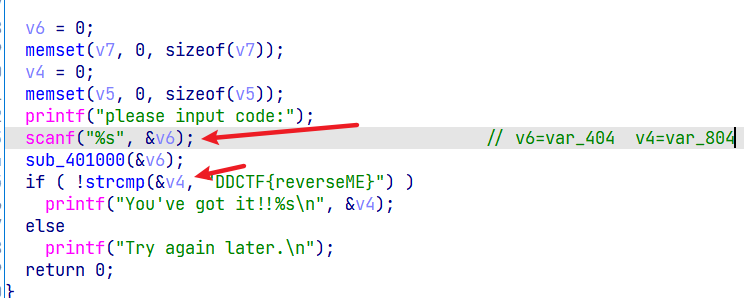
这里把v4给ecx
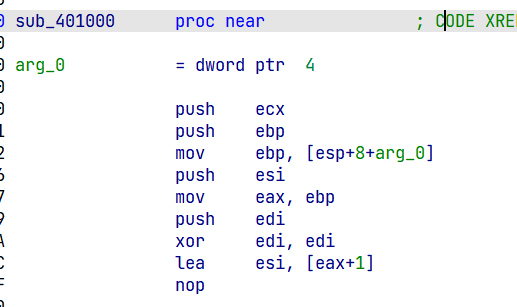
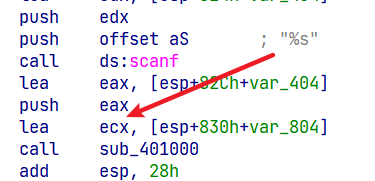
然后跳入sub_401000,并没有重新赋值ecx,
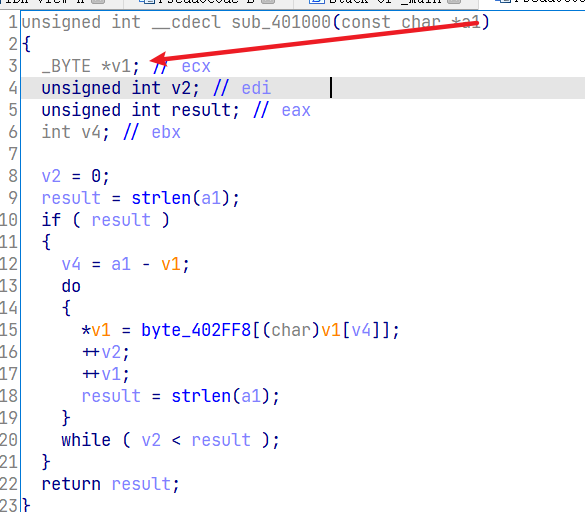
所以*v1=var_804
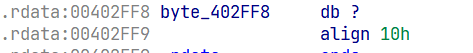
ascii 32位之前是不可视字符,所以有种情况是字符显示不出来,但实际有字符
dword=双字=四字节,正好等于一个地址0xAABBCCDD
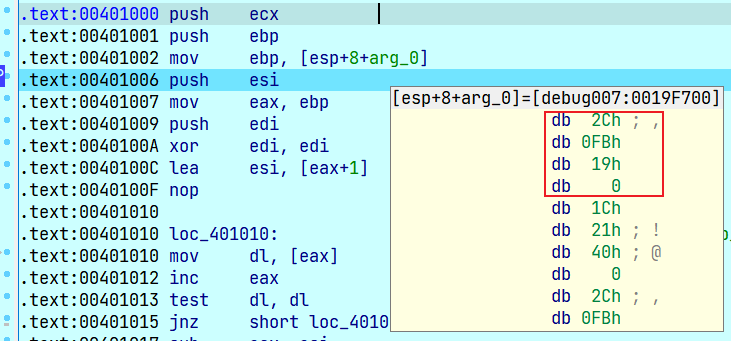
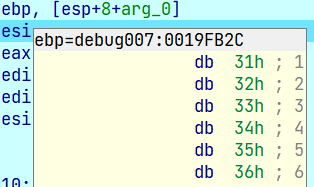
esp+8+arg_0=0019F700,
[0019F700]相当于取值,取这个地址里面的数据,而数据正好是0019FB2C,就是输入的字符串的地址
贴两个脚本
a = [126, 125, 124, 123, 122, 121, 120, 119, 118, 117,
116, 115, 114, 113, 112, 111, 110, 109, 108, 107,
106, 105, 104, 103, 102, 101, 100, 99, 98, 97,
96, 95, 94, 93, 92, 91, 90, 89, 88, 87,
86, 85, 84, 83, 82, 81, 80, 79, 78, 77,
76, 75, 74, 73, 72, 71, 70, 69, 68, 67,
66, 65, 64, 63, 62, 61, 60, 59, 58, 57,
56, 55, 54, 53, 52, 51, 50, 49, 48, 47,
46, 45, 44, 43, 42, 41, 40, 39, 38, 37,
36, 35, 34, 33, 32]
b = r"DDCTF{reverseME}"
for c in b:
tmp = ord(c)
for i in range(len(a)):
if a[i] == tmp:
print(chr(32+i), end='')hexData = [
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0xF8, 0xAE, 0x1D, 0x3E, 0x07, 0x51, 0xE2, 0xC1,
0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFE, 0xFF, 0xFF, 0xFF, 0x01, 0x00, 0x00, 0x00,
0x7E, 0x7D, 0x7C, 0x7B, 0x7A, 0x79, 0x78, 0x77, 0x76, 0x75, 0x74, 0x73, 0x72, 0x71, 0x70, 0x6F,
0x6E, 0x6D, 0x6C, 0x6B, 0x6A, 0x69, 0x68, 0x67, 0x66, 0x65, 0x64, 0x63, 0x62, 0x61, 0x60, 0x5F,
0x5E, 0x5D, 0x5C, 0x5B, 0x5A, 0x59, 0x58, 0x57, 0x56, 0x55, 0x54, 0x53, 0x52, 0x51, 0x50, 0x4F,
0x4E, 0x4D, 0x4C, 0x4B, 0x4A, 0x49, 0x48, 0x47, 0x46, 0x45, 0x44, 0x43, 0x42, 0x41, 0x40, 0x3F,
0x3E, 0x3D, 0x3C, 0x3B, 0x3A, 0x39, 0x38, 0x37, 0x36, 0x35, 0x34, 0x33, 0x32, 0x31, 0x30, 0x2F,
0x2E, 0x2D, 0x2C, 0x2B, 0x2A, 0x29, 0x28, 0x27, 0x26, 0x25, 0x24, 0x23, 0x22, 0x21, 0x20, 0x00,
0x01, 0x00, 0x00, 0x00, 0x90, 0x19, 0x9F, 0x00, 0xA8, 0x2C, 0x9F]
str = 'DDCTF{reverseME}'
flag = ''
for i in range(len(str)):
flag += chr(hexData[ord(str[i])])
print('flag{'+flag+'}')
![刷题笔记:[百越杯2018]crazy](/medias/featureimages/53.jpg)